It has been a REALLY spammy month here so I’m going to quickly go through this rogue’s gallery and give you the lowdown of what to watch out for and the best course of action. Plus I’ve got a doozy to start with.
Etta Avila sent me this one.
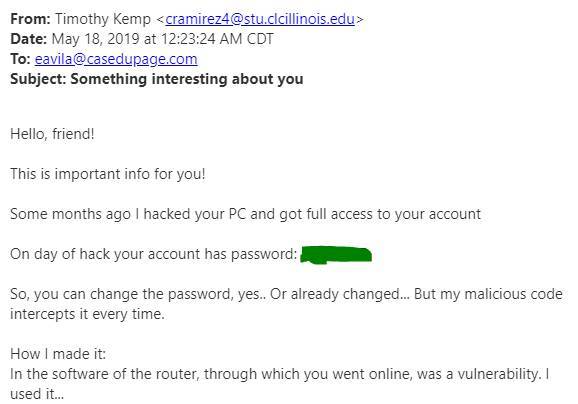
Some notes on this one:
- This is just like the one I blogged about in December: https://www.casedupage.com/spam-of-the-month-for-december-2018/ but with one important difference: It reported one of Etta’s REAL passwords that she uses for per personal accounts. Scary!
- The good news is that, no, the “hacker” didn’t actually hack Etta’s router.
- The bad news is that Etta’s password has probably been hacked and sold on the dark web as part of a package of stolen information. She will have to change that password and probably many others!
What you should do if you get SPAM like this (or even if you haven’t yet!):
- Surf to https://haveibeenpwned.com/ and input any emails or user account names that you use. If any of them have been “PWNed,” immediately change those passwords to something secure. You can’t go wrong with at least two full length random words with a random capital, number, and/or a symbol somewhere.
- Start recording your passwords using a service like LastPass (free) or 1Password (cheap), or use a password-protected Excel document in OneDrive (instructions).
You can read more about this attack here: https://botcrawl.com/14poc1jg97vuvsyokszyz7h276loazcrtn/
Here’s one from Melinda Smith:
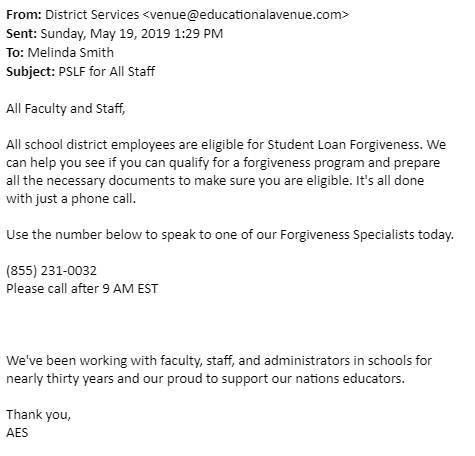
These are the same lovely people who have been spamming us with “Financial Services” ads for several months. The tricky thing about them is that they continually change the sender’s address so that Outlook can’t easily block them using the “Junk” button at the top. Fortunately, we can block them based on the content of the message (at the level of our Exchange server), and SolidState will do that for us when I ask.
If you get SPAM from AES, please make a ticket using https://support.caseil.com and I will pass it along SolidState to block for us. Thanks!
This one comes courtesy of Emily Shields:
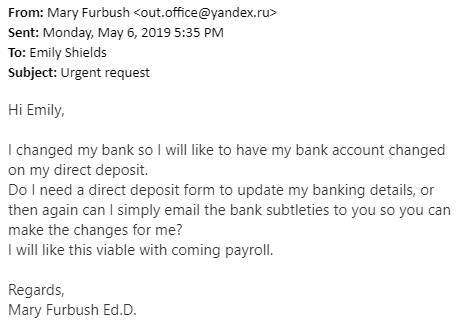
Wow, the Executive Director needs her bank account changed! How about that!
This is an example of spear phishing. The attackers did enough homework to know who CASE’s administrators are and they specifically wrote this email to mimic a reasonable request.
Some things to note:
- This email is well written from a scam point of view. It doesn’t have perfect grammar or spelling but neither do most of us when we write work emails to one-another.
- The biggest “tell” in this case is the sender’s address.

I’m pretty sure that’s not Mary’s address. Notice the “.ru” at the end–that’s a Russian domain. That doesn’t actually mean anything since it’s easy for anyone to create an email address with any domain, but it is kind of funny that the scammers left such an obvious clue.
The last one for this month comes from Jerry Brendel.
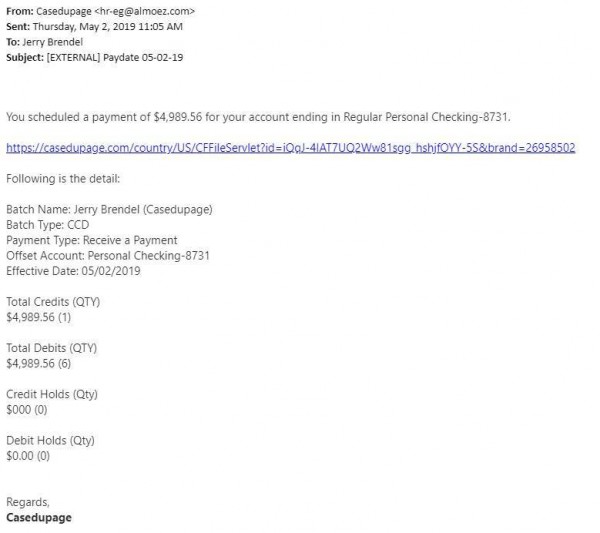
This is another example of spear phishing. It looks very official. Notice the web address right at the beginning: it starts with “https://www.casedupage.com” – that’s our website! If our Business Manager Jerry Brendel were less tech savvy, he might take that as a sign that this was legit. But watch what happens when we hover (DON’T CLICK) the mouse cursor over that link.

That’s not the same address! I don’t want to go to “bodycoat.in”!
When in doubt, never click on links inside of emails. But even if it could be legit, hover your mouse over the address and compare it to the address that appears in the footer of your Web browser.
And what do we say when the addresses don’t match?


