Sometimes, CASE staff send me fantastic examples of phishing and SPAM. Each month, I’ll highlight my favorites and show you what to watch out for.
Here’s a beauty, forwarded to me by Jerry Brendel, our Business Manager.
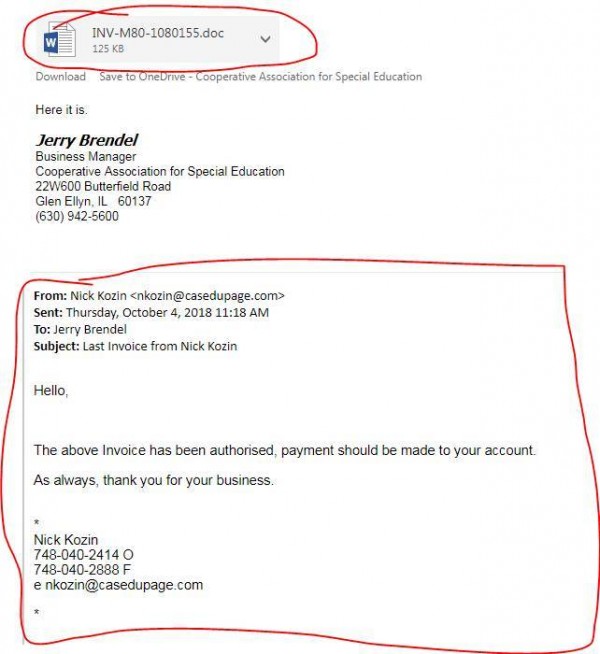
This is an example of both spear phishing and whale phishing.
It’s called “spear fishing” because the attackers took extra measures to make the email appear plausible. This in case, they spoofed the “From:” field to look like it is coming from a CASE employee, in this case the august Nick Kozin, who was my predecessor from several years ago. Spoofing refers to any hacking technique that involves replacing identifying information with false data.
It’s also called “whale phishing” because a Business Manager is a “whale”–a high-ranking administrator with access to valuable systems.
Notice the attachment. It is a virus disguised as a Word document. There are no obvious signs that it’s a virus–it looks like an ordinary “.doc” file. Word documents can contain macros that run hostile scripts on your computer. In this case, it was the Emotet trojan, which you can read more about here: https://twitter.com/WDSecurity/status/1046906416609484800 and here: https://www.us-cert.gov/ncas/alerts/TA18-201A

